NIST and CIS DRIVEN CYBERSECURITY SERVICES

Is your business secure?
TechHeights can help evaluate and mitigate
cybersecurity risks using proven NIST and CIS frameworks.
Small businesses (SMBs) might think they aren’t targets for attackers, but in fact, SMBs are the most lucrative targets. Without the right cybersecurity infrastructure in place, your SMB could be a primary target for hacking, phishing campaigns, malware, software exploits, ransomware and data breaches.
Whether it’s compliance, data protection, business continuity, or disaster recovery, we provide managed NIST framework cybersecurity infrastructure to stop numerous sophisticated attacks that plague SMBs. Our effective and scalable cybersecurity solutions protect from social engineering, phishing, brute-force password attacks, malware, ransomware, insider threats, advanced persistent threats (APTs), botnets, distributed denial-of-service (DDoS), and many more.
We support dynamic and unique business environments often found in SMBs, but our primary managed cybersecurity services include:
- Security operations center (SOC)
- Cybersecurity awareness training for employees, contractors, and key vendors
- Endpoint Detection and Response (EDR) and advanced Extended Detection Response (XDR)
- Email hygiene and filtering services to block spam, phishing, and malware
- DNS filtering or content filtering
- Penetration testing and vulnerability scanning
- Security architecture and deployments of cybersecurity infrastructure
- Incident response to cyber-attacks and malware
Get In Touch
We can help. More productivity and network security, reduced IT cost, and regulatory compliance – all of these are benefits we provide to our clients. Want to know more? Contact us today!
Our cybersecurity framework includes multi-layers of protection
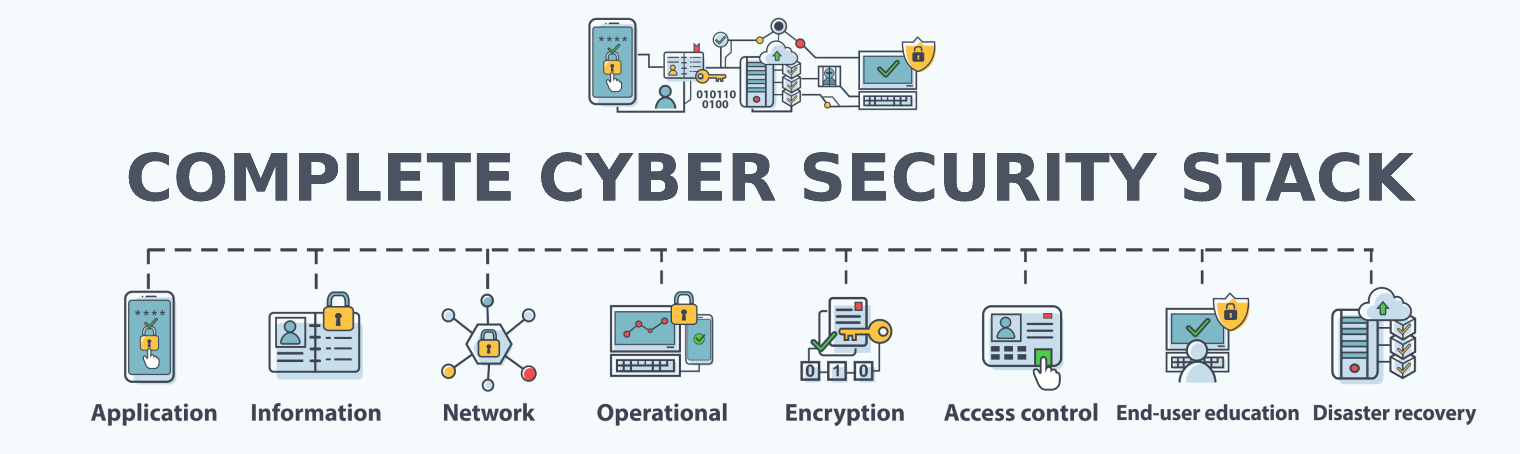

We help SMBs stay compliant with several regulatory standards including:
- Cybersecurity Maturity Model Certification (CMMC)
- National Institute of Standards and Technology (NIST)
- Financial Industry Regulatory Authority (FINRA)
- Health Insurance Portability and Accountability Act (HIPAA)
- International Traffic in Arms Regulations (ITAR)
- Payment Card Industry Data Security Standard (PCI-DSS)
OUR RESULTS ORIENTED CYBERSECURITY PROGRAM
Step 1: Security Posture and Security Maturity Level Assessment
The first step in securing your business is assessing your current cybersecurity posture. A Security Maturity Level Assessment (SMLA) is standard practice for every business to evaluate its current cybersecurity infrastructure, access controls, and current levels of risk. Performing a proper SMLA requires the right professionals who know how to carry out an assessment and deliver a plan of action.
Our assessment professionals will:
- Review your current security policies and procedures
- Interview stakeholders, executives, IT, and other users integral to your cybersecurity posture
- View your security access controls and current methods used to protect data
- Review your compliance procedures and ensure that you are not violating any regulations
After our assessment, you receive a score to explain your maturity level. As a trusted NIST provider, we use this assessment to develop a strategic plan to tighten security and reduce business risks. We provide a full report of your current risk factors and provide recommendations to improve your policies.

Step 2: Develop a Security Plan That Fits Your Budget
Once you’re aware of your current risks, we help develop a security plan within your budget and target timeline. Our professionals work directly with key stakeholders to build a scalable, effective solution. Every organization has a unique environment that requires the right plan, and we will customize a strategy that addresses your unique requirements, budget, concerns, and deadlines.

Step 3: Implement Your Custom Security Plan
The final stage is implementing your security plan. Our professionals will work with you to create a timeline and limit downtime as much as possible so that the deployment of cybersecurity infrastructure does not affect business productivity. Implementation is unique to your environment and plan, but generally, we will:
- Deploy compliant monitoring systems to detect malicious activity from insider and outsider threats.
- Install a vulnerability management system to reduce risks of known exploits across hardware and software.
- Provision and install endpoint security protection for user devices, servers, workstations, and other potential targets.
- Apply secure access controls to your sensitive files and data.
After the implementation of your security plan, we continue to maintain resources and regularly review them for any upgrades or necessary changes. We continue to support your business after controls are put in place so that you can get the most out of your cybersecurity. We will:
- Review your policies and procedures to identify any areas that could be improved.
- Run reports for stakeholders to read so that they understand what your cybersecurity controls do for your business and how often it protects from a data breach.
- 24x7x365 monitoring and administration
- Respond, contain, and remediate threats using our SOC monitoring. We also help administrators perform thorough incident response and alert them to detected threats.







