by techheights | Apr 7, 2023
In 2021, the Federal Trade Commission (FTC) amended the Gramm-Leach-Bliley Act, which is commonly known as the “Safeguards Rule.” The amendment, which goes into effect on June 9, 2023, creates stricter regulations for car dealership data protection. The rule requires dealerships with over 5,000 customer records to develop, implement, and maintain a security program to protect customer information. If you’re a small dealer, you might wonder how you can contend with these big changes. In this guide, we’ll outline the new regulations and discuss how a managed services provider in Orange County, like TechHeights, can help car dealerships get compliant before the upcoming deadline.
What Are the FTC Regulation Changes for Car Dealerships?
Car dealerships handle a large volume of consumer information, including sensitive data that cybercriminals want to steal. The Safeguards Rule outlines stricter procedures that dealerships must follow to protect their customers’ information and reduce the possibility of a cyberattack. Before the amendment, the FTC allowed dealerships to make their own protections. However, with the rise of cybercrimes, the revised rule provides more concrete guidance for dealerships’ security programs.
Updates to the Safeguard Rule
The new Safeguards Rule identifies nine key elements that your car dealership’s information security program must include:
- Designate a “Qualified Individual” to implement and supervise the dealership’s information security program. This person can be an employee or can work for an IT service provider in Orange County, like TechHeights.
- Conduct a risk assessment. Before creating a compliant security program, dealerships must first understand what information they have, where this information is located, and which specific threats could affect the data’s security.
- Implement safeguards to control the identified risks. This part of the rule is very detailed and includes specifics on access management, encrypting sensitive information, implementing multi-factor authentication, and securely disposing of information.
- Assess vulnerabilities and continuously monitor the effectiveness of these safeguards.
- Train your employees. Staff members need regular, specialized training to spot potential risks.
- Monitor service providers. Your dealership probably works with multiple vendors to run your business as smoothly as possible. But under the new rule, your service provider contracts must include security expectations, including security assessments.
- Keep your information security program current. Dealerships must adjust digital security programs based on any changes.
- Write an incident response and recovery plan. The plan must outline procedures, processes, roles and responsibilities in case of a security event.
- Require the “Qualified individual” to provide a regular written status report on the company’s security program.
How Can a Managed Service Provider Help Car Dealerships Stay Compliant?
The changes to the Safeguard Rule are complex and time-consuming. Many of the requirements listed above have detailed specifics, and all of them require most car dealerships to develop new expertise and capabilities — and fast. A managed service provider in Orange County can be a trusted partner in helping you create a culture of cybersecurity awareness. TechHeights helps car dealerships stay compliant in a variety of ways, including:
- Assessments: We’ll guide you through the process and perform a detailed analysis to determine your current level of compliance.
- Recommendations: After the assessment, we’ll give your dealership specific guidance on how to build and implement a compliant information security program.
- Training: We can provide cybersecurity awareness training to your employees, contractors, and vendors.
- Monitoring: TechHeights offers continuous security monitoring to detect potential cyber security threats and vulnerabilities.
Our certified experts understand that the new FTC regulations create significant challenges for small car dealerships. Contact TechHeights today for expert help tailored to these new requirements for car dealerships.
by techheights | Apr 7, 2023
2022 was a turbulent year for cybersecurity. Several large companies, including Twitter and Uber, made headlines after experiencing data breaches. While it’s true that high-profile breaches grab the media spotlight, it doesn’t mean that small businesses are free from cybersecurity concerns, either. In fact, the opposite is true. Small businesses are increasingly becoming attractive targets for hackers.
No matter the size of your company, digital security is an essential part of your business operations. Let’s look at what cybersecurity is and why every small business needs a strong cybersecurity presence.
What Is Cybersecurity?
Cybersecurity, which is also called Information Technology (IT) security, protects critical systems, networks, and information against digital breaches or cyberattacks.
Cyberattacks usually try to steal sensitive data, extort money, or damage an organization’s computers. Criminals use several methods to carry out cyberattacks, but the most common for small businesses are email phishing and malware.
The good news is that you have the power to fight back. A strong cybersecurity strategy protects your valuable assets, empowers your employees, and increases consumer trust in your business. However, cybersecurity isn’t a one-time implementation or training. Instead, effective cybersecurity is an ongoing process for any small business.
The Importance of Cybersecurity for Small Businesses
As cyber threats increase in size and scope, more enterprises are investing in cybersecurity tools. As they strengthen their security postures, hackers are pivoting toward easier targets: small businesses. Unfortunately, cyber attacks against small businesses are becoming increasingly common. As of 2021, 46% of all data breaches targeted small to medium-sized companies with fewer than 1,000 employees.
Of course, the financial ramifications of an attack can have a big impact on high-profile enterprises. But one breach can sink a small company, which is why cybersecurity is so important for small businesses.
Why Do Cybercriminals Target Small Businesses?
Hackers go after small businesses for three main reasons.
Fewer Resources
Small businesses are responsible for protecting customer data, including personally identifiable information (PII). However, unlike large enterprises, small businesses often don’t have the resources to safeguard this data against evolving cyber threats. Hackers know this, and they also know that small business employees might lack the cybersecurity training to recognize an attack in the making.
Cybercriminals are becoming more sophisticated in their attack methods. They commonly use various types of social engineering attacks, like email phishing, to target smaller businesses for one simple reason: they work. The average employee of a business with fewer than 100 employees will experience 350% more social engineering attacks than an employee at a bigger company.
The Rapid Growth of Technology and IoT
As the use of technology increases, more small companies rely on IoT devices to optimize their operations. However, as their network of smart devices grows, so do potential threats. Most IoT devices lack built-in security and allow remote access, which creates more security vulnerabilities for small businesses.
Links To Bigger Companies
Small businesses are often digitally linked to larger companies for various purposes. Hackers might not be able to penetrate the defenses of the larger organization, so they go after the small businesses that support them instead. For example, consider the massive Target breach in 2014: hackers accessed the network using login credentials stolen from Target’s HVAC partner.
How Do I Learn More About Cybersecurity for My Small Business?
If your business uses the internet, you need to create and maintain an effective cybersecurity plan. The good news is that you don’t have to do it alone. TechHeights offers the best-managed IT services in Orange County. Our experts understand the cybersecurity needs of small businesses and support your business when you need it the most. Contact us today to see how a custom cybersecurity framework can help your small business thrive.
Facebook Post
While it’s true that high-profile companies grab the media spotlight, it doesn’t mean that small businesses are free from cybersecurity concerns. In fact, the opposite is true. Small businesses are increasingly becoming attractive targets for hackers.
So, why do cybercriminals target small businesses? It comes down to three things:
- Small businesses have fewer resources
- They’re using more technology than ever before
- Small businesses are often linked to bigger enterprises
Check out TechHeights’ latest blog to learn how cybersecurity can help small businesses beat the bad guys.

by techheights | May 23, 2022
For the last couple of years, providers offering Managed IT Services in Riverside have become prevalent among small and large businesses. After all, everyone wants a professional helping hand capable of taking care of their day-to-day IT needs. And while there are various benefits of hiring these services, one can wonder – are these Managed IT Service providers safe for their organization’s safety? Yes, they are!
Today, we are here to discuss why we think you can rely upon these experts for safety. So let’s get started!
Reasons Why Such Services Providers Are Safe For Your Organization
We cannot say that all IT service providers will be safe. But most of these are considered very professional and secure while handling an organization’s security and IT needs.
Here are some of the reasons. Read on!
- Firstly, whenever you think an IT service provider might be unsafe for your organization, it is necessary to remember that all these MSPs have multiple cybersecurity layers. And most of the time, their security system is much more secure than the system your company is using right now. So you do not have to worry about your information being leaked to a third party or hacked.
These levels of cybersecurity include various applications, firewalls, and more for the constant monitoring and protection of important and sensitive data.
- Data hacking, application failures, or complete network collapse can affect any organization. And the repercussions of these failures can be catastrophic. If you engage an external company to address your IT needs, they will take care of every aspect, including backing up and syncing data to ensure minimum downtime. Experts plan and implement several useful tools to help businesses recover from a malicious cyberattack and tech disaster.
- Top-notch and upgraded technology systems help businesses achieve operational efficiencies and improved productivity. No matter the extent of your business and what computer or network system your firm uses, after some time, IT equipment will require upgrades, maintenance, and repair to ensure continuous workflow. Tech experts employ reliable, proactive solutions to keep your systems and network running at optimum levels.
Note
While we ensure that IT services in Santa Ana will be safe for your organization, we always suggest choosing someone experienced and reliable. These factors will contribute to their professionalism and ensure that they take your organization’s safety very seriously.
We suggest checking an IT service provider’s online reputation before hiring them for the best results. Check out their social media pages, LinkedIn profile, and Google reviews. These reviews will tell you whether other customers found them safe and reliable.
Conclusion
Thus, we can conclude that a managed IT services provider is safe for your organization’s safety. Moreover, experienced professionals take their jobs seriously and will not disappoint you. So what are you waiting for? Outsource your company’s IT handlings today. We, TechHeights, have been in the business for many years and have helped many businesses flourish with the best IT support. Whether you need complete network installations, system maintenance & upgrades, network security & compliance, or cloud services in Orange County, we can help. Call (888) 600-6070 for a free assessment
Tags: Cloud Services Orange County, IT Services Santa Ana, IT Support Orange County, Managed IT Services Riverside

by techheights | Feb 27, 2022
Cybersecurity Maturity Model Certification (CMMC) is a security protocol program devised by the U. S. Department of Defense (DoD) back in 2019. It is a certification process that lays out a contractor’s safety essentials.
Stats suggested that more than 65000 companies would have to comply with such certification in the forthcoming years. Therefore, having experienced IT Support, Irvine, is imperative, looking at its emerging importance.
CMMC is an assortment and a kind of addition to extant regulations. However, International Traffic in Arms Regulations (ITAR) will remain a distinct certification from CMMC – however, ITAR Compliant firms will also mandate to abide by CMMC.
CMMC Notables
- Generically, there are five levels of the security maturity process rising from ascending order.
- Unlike NIST, there is no self-evaluation. Therefore firms require to get authorized through qualified IT Services Irvine
- Any firm that presently performs business with DoD will comply with CMMC – and that signifies direct DoD contractors and high-level CMMC firms’ supply chains should also adhere to, at minimum, ground-level essentials.
- DoD would publicize all contractor’s certification level essentials.
Does CMMC influence my Firm?
This is readily responded with a 2-part query:
1) Is your firm a direct contractor to the DoD, or
2) Does your firm make a trade with a contractor to the DoD* firm?
If you replied “yes” to contest 1, your firm would require to be CMMC compliant. Likewise, if you replied “yes” to the second one, your firm will probably require CMMC compliance.
5 Levels CMMC
- Level 1 – “Basic Cyber Hygiene”
This includes meeting the requirements of 48 CFR 52.204-21, antivirus, and more.
- Level 2 – “Intermediate Cyber Hygiene”
This involves risk management, abiding by documented SOP, setting up Back-Up / Disaster Recovery (BDR), and furnishing user awareness and training.
- Level 3 – “Good Cyber Hygiene”
This includes Multi-factor Authentication of the systems, security compliance with all NIST SP 800-171 Rev 1, and building security to fend against Advanced Persistent Threats (APTs).
Level four includes network segmentation, mobile device inclusion, chamber detonation, use of DLP technologies, and more. It even comprises of setting up adequate security and embracing tactics and procedures.
- Level 5 – “Advanced / Progressive”
Level 5 is all about device authentication, cyber maneuver operations, and organization-wide standardized implementation of security protocols. It even concerns 24/7 Security Operations Center (SOC) Operation and real-time assets tracking.
The most important thing about CMMC is that it requires certification from a licensed 3rd-party CMMC company, unlike NIST. Presently, most organizations can self-certify for DoD-related securities. However, it is still better to hire Managed IT Services in Irvine to ensure all needed requirements are duly met.
Final Words
So, do you have any queries related to CMMC? Or are you looking for help to efficiently make a way out? Or are you facing any other cybersecurity, compliance, or data issues? If yes, reach out to TechHeights today!
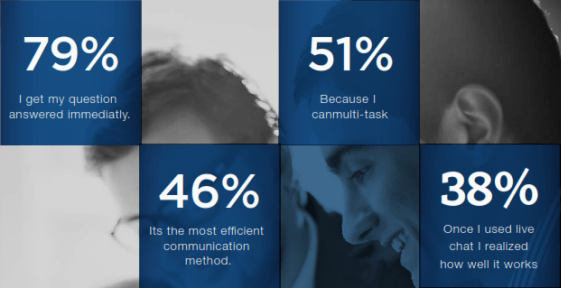
by techheights | Sep 6, 2017
Many organizations assume that providing live chat while offering tech support in Orange County is a choice. But we think it’s a necessity. How? Let’s take an example. Imagine walking into a grocery store and finding no support staff to help you find the stuff you need. Sounds horrible, right? In such a situation, a customer will just go to another store and the first grocery store will lose a customer. The case is the same in tech support. If the customer can’t reach a qualified person to resolve a glitch instantly, you will lose a customer.
If you are still not convinced on why offering live chat as a part of tech support in Orange County is essential then the below-mentioned points might help you.
Live chat is a quicker option for the customer to reach you and for you to reach the customer. When you have a chat session with the customer, you can not only solve their IT glitches, but you can also sell your services to the customers. You can also get their approval to buy a service much quicker than an email because the decision-making process is quite fast when the customer is getting quick service.
Live chat while providing tech support in Orange County is also essential because it lets your customers get the answers they need without waiting. Unlike a call, they don’t have to wait for a tech support provider to get some advice. It’s the opposite, the tech expert can resolve multiple issues at once and the time needed to solve a problem is just a few minutes.
Customers don’t like to repeat their problem repeatedly, and while using live chat, they don’t have to. Even if a problem is not solved by one expert, the other can come in, read the issue in the chat box and offer a solution without even the need to consult the first expert. It makes your tech support in Orange County more efficient.
A benefit of using live chat for providing tech support in Orange County is that the customer can avail it at any time of day or night without disturbing the people in his or her household (which might happen on a phone call). The email also assures no disturbance, but it’s not that quick as a customer might have to wait for 24 hours to get a response.
Finally, live chat is a useful tool for a company as well as the customer because every conversation is recorded at both ends and this conversation can be accessed if a similar problem occurs in the future. Easy record keeping also helps a company to exactly count the time taken to resolve the issue by eliminating time spent in pleasantries.
Are you aware of more cool reasons to provide live chat during tech support in Orange County? Do let us know in the comments below!
Tags: Tech Support in Orange County

by techheights | May 23, 2017
Imagine you are running a successful business, clients keep coming in and you have a lot of work to do but your IT system crashes or hangs over and over again. Won’t you feel frustrated? Won’t you ask yourself why didn’t you set aside some money to pay for quality tech support in Orange County? If so, it’s time to save yourself from such an annoying situation and hire tech support in Orange County so your business can run smoothly for long without any IT glitches. Here are a few reasons why hiring tech support in Orange County by trusting a company like TechHeights is a smart move.
Same Day Service
When you retain a tech support service provider, you will not have to waste time in hunting up an expert and then wait for the expert to come in and solve the problem. The experts will be at your beck and call. In most cases, you will get the same day service and the issue might be resolved in a few minutes.
Stretching Your Dollars
If you hire a trustworthy, reliable and ethical company for tech support in Orange County where clients are always given the first priority, you will get to save a few bucks. The company people will know of cheap & reliable ways of fixing your IT issues and they will not offer overpriced solutions that may ruin your budget.
Cost-Effective Solutions
A team of IT experts would also offer multiple packages and you will have the power to pick the one that suits you best. Thanks to these package options, you will pay for only the services you really need and you won’t pay for a service you don’t need or want.
Size Doesn’t Matter
While seeking tech support in Orange County, you should hire a firm that has a lot of experience and relevant certifications. It will ensure that they have the capacity to solve a problem of any magnitude in a flawless manner. A good company offering these services would also be happy to pay you a visit regarding simplest problems without making a fuss about it.
Business Enhancement
Finally, when you opt for the right kind of tech support in Orange County, you will get some invaluable advice from the IT professionals on how you can enhance your IT Infrastructure to meet the current and future needs of your end-users and the clients. There will usually be no pressure to enhance the technologies but if you follow some of the suggestions, your business will be future-ready.
Tags: Tech Support, techheights





Recent Comments